SSH server security through obscurity
The openSSH server allows you to connect to a remote server (eg a Linux or BSD machine) in a terminal session and run command line applications etc. By default SSH servers listen on port 22 and this is the source for a number of brute force attacks as people try to log into remote servers to do nasty stuff. There are a number of methods for securing SSH better (eg firewalling out access to only a limited set of hosts, using RSA/DSA keys and so on) but we'll look at those another time. This post is about «security through obscurity» where we configure the SSH server to listen on a different port than port 22.
The SSH server configuration file is usually located somewhere like /etc/ssh/sshd_config . As the root user, or running the sudo command, we want to open up this file and make a very minor change.
Find the following line:
Port 22
comment it out and add a new line with some random port number, eg 58291. The maximum number the port can be is 65535, and you want to make sure it's not set to some other commonly used port number such as 3306 for MySQL otherwise you may cause problems further down the track. After making the modification that section of the SSHD config file will look like this:
#Port 22 Port 58291
Now you just need to restart the SSH server and it will now be listening to the new port instead of the default port (the actual filename of the init script might be different — the two below are fairly common):
/etc/init.d/ssh restart OR /etc/init.d/sshd restart
Connecting to the SSH server on a differernt port
So now that we have the SSH server listening on a different port, how do we connect to it? If we try to connect using the ssh command line tool then it will attempt to use the default port, and you'll end up with an error along these lines:
$ ssh putty.org.ru ssh: connect to host putty.org.ru port 22: Connection refused
Instead you need to pass the port number to the ssh client on the command line with the -p command line argument like so:
$ ssh -p 58291 putty.org.ru
Now you should be able to connect.
If you were using the free SSH client Putty, then you would specify the port as shown in the example screenshot below:
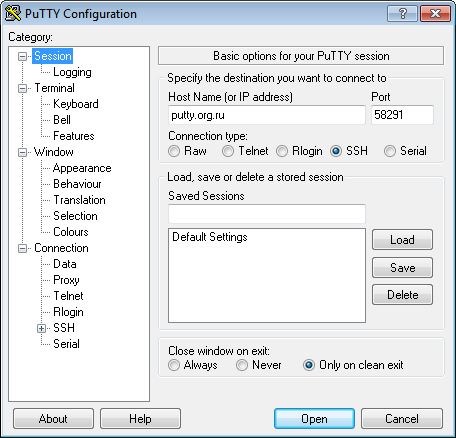
This is not a complete solution for SSH security. Ideally if SSH access is only required from a limited number of addresses then you should use other means to secure the server for SSH access to only those addresses, and/or use RSA/DSA keys. However it can be a useful way to stop brute force attempts to log into your server if you can't do this.